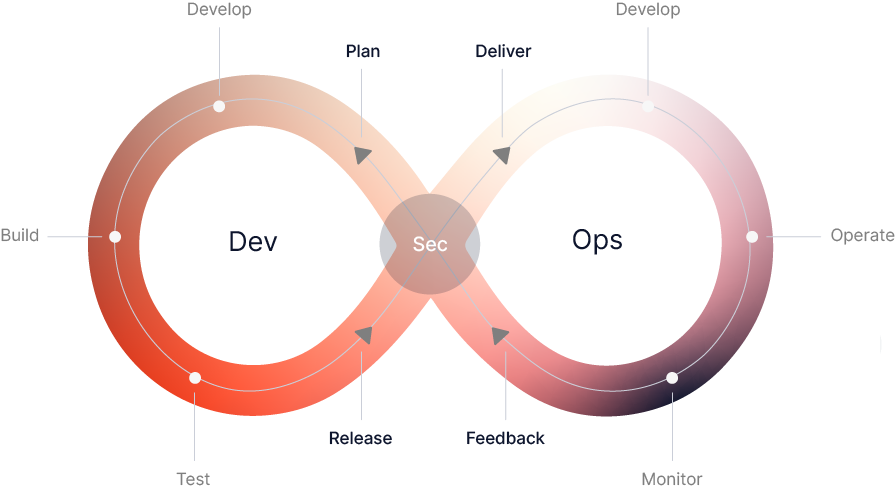
DevSecOps-as-a-Service
Achieve excellence in continuous delivery through Secure DevOps-as-a-Service
Industry Challenges
Building a secure CICD Pipeline
Build unified, Secure Continuous Integration and Continuous Deployment process. Pick tools that align with existing applications and business processes.
Centralized Logging, monitoring, automated updates
Integrate your development and deployment processes with end-to-end security, centralized logging & monitoring, and automated software provisioning.
Replicate and Secure Infrastructure
Use Infrastructure-as-a-Code to recover and replicate a similar infrastructure, improving business continuity.
Securely Migrate from Monolithic to Microservices
Securely transform legacy monolithic applications to microservices and API-based environments by augmenting security tools and technologies.
Solutions
Our DevSecOps-as-a-Service model allows you to augment your team with our top-tier engineers who work with your team to secure code, tools, and technologies. Keeping security as part of the architecture and following design thinking patterns, our engineers help you to combine development and deployment operations.

Code Analysis
Identify vulnerabilities by submitting small functional pieces of code.

Vulnerability Management
Identity and manage threats continuously during the development phase and prioritize the mitigation.

Change Management
Apply change management practices using tools and technologies so overall changes can be tracked.

Log Management & Monitoring
Manage logs using the industry’s best log management and monitoring tools that allow excellent visibility into potential security threats.

Network and Service Hardening
Secure your microservices and API layers by employing secure-by-design practices and continuously scanning the services for potential security threats.

Identity, Access (IAM), and Secrets Management
Integrate your software infrastructure with secret vaults managers, multi-factor authentication, authorization, and Single Sign-On and enforce least privileged access control.

Container Management
Mitigate security risks by using best practices for your Docker and Kubernetes. Deploy container security tools that help manage policies, access management, and increase visibility into cross-container communication.

Compliance
Comply with industry-standard, e.g., OWASP, CIS, NIST, HIPAA, and PCI, leading to overall organizational compliance initiatives.
Our Approach
Comprehensive Security Assessment of Development Processes and Architecture
Development of Security Architecture and Orchestration of Tools and Technologies
Integration with DevOps Pipeline
Comprehensive Security Assessment of Development Processes and Architecture
Development of Security Architecture and Orchestration of Tools and Technologies
Integration with DevOps Pipeline
Supported Tools



























Case Studies
FAQs
Let us help you with any inquiry you might have.
What Is DevSecOps and How Does It Work?
DevSecOps is the convergence of development and security, bringing the two roles closer together. The goal is to incorporate security into every step of the software development cycle. This allows for a rapid release of applications, ensuring that they’re secure.
A security-first approach reduces the chances of data exposed to a malicious entity. In addition, implementing a DevOps strategy in your organization can improve overall productivity and customer satisfaction. With more automation and faster feedback loops, you can do more in less time.
The first step in planning for a security-first development process is to establish a threat model and acceptance test criteria. These will help to identify vulnerabilities and provide guidelines for developers to follow.
For security to be a part of your development team, the entire team needs to be familiar with the fundamentals of security. It’s also important to understand that a DevOps environment can’t exist without motivated people. If your team members are unable to keep up with the pace, you’ll need to train them.
DevOps tools, like automated security controls, can ensure that your application is deliver in a timely fashion. This helps to avoid expensive fixes after the fact.
DevOps helps teams collaborate with one another, resulting in a more efficient workplace. Developers can receive timely feedback and learn from their mistakes, which empowers them to write secure code.
How DevSecOps Enables High-Velocity Digital Transformation?
The adoption of DevOps has brought about a shift in the way security is built into the SDLC. Security now incorporated into the planning, design, and implementation stages. This means that security weaknesses immediately spotted and fixed during the development cycle.
With the use of common tools and practices across the software delivery lifecycle, development teams can increase innovation velocity and build systems with reliability and quality. Additionally, the integration of DevOps and CI/CD tools enhances compliance and cybersecurity.
DevSecOps has adopted by many global enterprises. In the healthcare industry, for example, the technology has been employed to automate and streamline assisted processes. Other organizations, including Adobe and Facebook, have used the process to accelerate their development cycles.
One of the most defining characteristics of DevOps is the collaboration that takes place between development and operations teams. This collaboration has reduced time and costs and increased performance.
Another key factor in enabling the adoption of DevSecOps is visibility. Continuous Monitoring, which is perform to monitor application performance, is a vital stage in the DevOps lifecycle.
How to Successfully Transition to DevSecOps?
In order to transition to DevSecOps, your organization must adopt a new mindset. A culture of transparency and shared intelligence will be critical. The more teams work together, the less likely there will be a breach.
For successful DevSecOps implementation, your organization will need to add tools and processes that will help security operations and development teams. These include training, traceability and communication.
To transition to DevSecOps, it’s important to understand how to get buy-in from teams throughout the company. It’s also vital to understand that this isn’t an overnight process. As with any change, it takes time and patience to implement the new processes.
Your organization may need to take a phased approach to transition to DevSecOps. This will help ensure that you are able to make improvements along the way. Phased implementation can also help ensure that you are able to gather input from all involved parties.
Your team should have a system in place to carry out code audits on a daily basis. Every new commit should analyze to prevent malicious code from entering the system.
Developers should retrain to avoid creating unreliable code. They should also train to perform security tasks and use the right tools.
Security operations should consult early and often by the IT department. This will allow them to find vulnerabilities and fix them before they become a problem.
Security should incorporate into the CI/CD pipeline in order to ensure speed and consistency. Creating templates will also ensure repeatability and consistency.
Is DevSecOps Really Important in Businesses Nowadays?
DevSecOps is an approach to security that seeks to address security issues before they become a problem for the application. It also aims to create a culture where developers and security experts can work together. This collaboration reduces the risk of breaches to both internal networks and the delivered product.
As an advocate of a secure software development lifecycle, Liz Rice encourages companies to adopt new working styles, invest in education, and adopt new tools. One tool that she suggests is CI/CD, which is an effective way to build a unified workflow.
Traditional security controls are based on legacy practices, and they don’t keep up with high-speed continuous delivery software development. In addition, they’re not equipped to provide front-to-back protection. That’s why security must embedded into the system, and it’s crucial to have a unified approach throughout the entire app lifecycle.
Security automation is critical to the success of DevSecOps. Automated security testing can help identify security vulnerabilities before they enter the production environment. By reducing the time spent in development, this allows teams to quickly respond to problems.
Security issues before they reach the production environment are less expensive to fix. For example, hackers often seek ways to gain access to a business’ software applications. Without a comprehensive security strategy, they could end up having a huge impact on the organization.
With a unified approach to security throughout the product development lifecycle, businesses can build high-quality software at a faster rate. The most important goal is learning from an incident, not just preventing it from happening.
What Are DevSecOps Best Practices?
A key aspect of DevSecOps is educating developers on security best practices. This can happen through a variety of means. Educational materials can send to developers, as well as through seminars.
Another way to create a secure environment is to avoid code dependency. Developers should not have access to code repositories unless they authorized. They should also only use third party software that has tested for security vulnerabilities.
Ensure your development team is up-to-date on the latest application security tools. This includes registering the applications for security vulnerabilities, scanning base images, and implementing secure password practices.
A secure password practice involves using secure password managers, avoiding common passwords, and keeping passwords updated. You should also ensure the CI/CD build infrastructure is secure.
The best practices for DevSecOps should integrated into your workflow. For example, you can implement a SAST tool for catching SQL injection issues. These tools can incorporate into the build pipeline for each phase.
The ideal technique for securely sharing secrets is a synchronized, encrypted secrets store. Registries are also a great option, but these should access by only authorized developers.
Issue tracking is another important tool for improving DevSecOps practices. These tools can gather data and provide targeted feedback to developers.
What Are the Key Components of DevSecOps?
Security should consider early in the development process. It should include in the product’s design and it should be a part of every team’s work. However, the reluctance of people to change can be a speed bump. This is why organizations need to train people and provide support for new processes.
For security professionals, it is imperative to participate in the development process and contribute to the creation of user stories. Moreover, they must give the time they need to implement new security protocols. In this way, they can help make security a part of the company’s culture.
DevSecOps teams may need to invest in new tools. Automated code scanning tools, for example, can search for security defects. Some open-source tools even offer automatic defect remediation.
During the plan phase, developers and security professionals will work together to establish shared goals, processes, and metrics. The result is a modern, streamlined software development CI/CD pipeline.
At the release phase, the security team will assess the runtime environment and network firewall access. They will also examine secret data management and user access control. If a problem found, the issue will report to the developer.
How to Automate Security Testing With DevSecOps?
Developers can train to incorporate security controls into their code, while also helping operations teams to respond to alerts from security tools. Security tools can scan third party components and open-source components for vulnerabilities. Using automated testing can help developers identify vulnerabilities and ensure the code is secure.
Security professionals need to establish threat models, user designs, and acceptance test criteria. To achieve this, they must be knowledgeable about the current cybersecurity threats and how to conduct risk assessments.
Getting buy-in from teams and senior management is a difficult challenge. However, the advantages of adopting DevOps are substantial. Among them are improved productivity, increased customer satisfaction, and a faster time to market.
Despite the benefits of adopting DevSecOps, there are also many misconceptions. For instance, many DevOps teams believe that security assessment slows down the workflow. That may be true in some cases, but it’s possible to avoid this issue by using the right tools and processes.
One of the most important components of the DevSecOps process is documentation. Documenting processes and security requirements in plain language can help development teams learn from their mistakes. This information can then use to improve code quality and minimize the risk of security breaches.
What is the Difference Between DevOps and DevSecOps?
DevOps and DevSecOps are two separate but complementary approaches to software development. Both are aim at bringing teams together, making the most of their talents, and creating high-quality products. Choosing which approach to use depends on the needs of your organization.
DevOps is a set of practices designed to improve the efficiency and speed of software delivery. Teams that work together to achieve these goals can get more tasks done in less time. As a result, organizations can run more product releases, improving the quality of applications.
DevOps and DevSecOps have similar security practices. For example, both use automation to help with deployments and security reviews. Similarly, both use a Continuous Integration (CI)/Continuous Deployment (CD) pipeline to speed up the software delivery process.
One key difference between DevOps and DevSecOps is the way they handle collaboration. In DevOps, developers and operations teams work together to deliver the best possible software. On the other hand, in DevSecOps, the security professionals are introducing early in the software development process.
How Does DevSecOps Support Digital Transformation?
If your organization is struggling to keep up with digital transformation, DevSecOps can be a big help. It focuses on security as an integrated part of the software development pipeline. This allows application developers to spot vulnerabilities before hackers exploit them.
The benefits of using DevSecOps include reduced cycle times, a more flexible workforce, and improved collaboration. However, the approach is not without its challenges.





