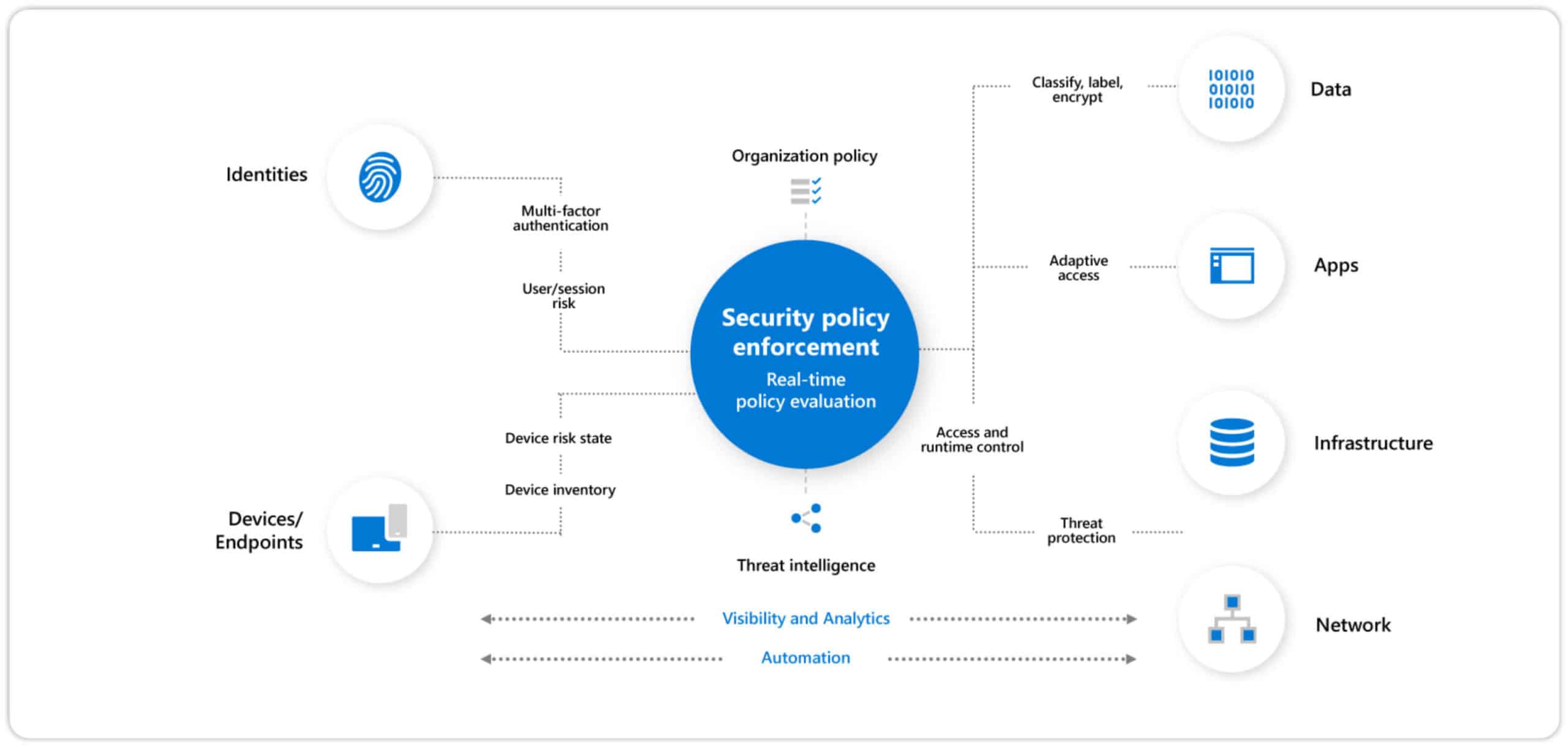
The best active defense strategies for Kaseya style ransomware attacks aren’t just firewalls and anti-virus. They’re active defense strategies. These involve exploiting the initial access vector, establishing zero trust, and creating a centralized data defense strategy.
Zero trust security
One of the most required active defense strategies for Kaseya style ransomware attacks is the supply chain attack. The attack hit more than 1,000 businesses across several countries, including supermarkets, retail stores, and software vendors. In the aftermath of the attack, several companies forced to shut down their operations.
The security community is beginning to see more and more implications of the growing number of ransomware attacks. In addition, bad actors are refining their methods to attack networks more effectively. These new tactics, such as double extortion, increase the odds that a business will pay the ransom.
To protect against Kaseya style supply chain attacks, companies should consider using a Zero Trust security model. This model provides automated protection to prevent malicious actions against assets on premise and in the cloud. It also limits the attacker’s access to critical systems and reduces the severity of a ransomware attack.
Internal data defense strategy
Ransomware has become a very powerful cyber weapon. It can disrupt services and steal data. However, if the attack not detected early, it can lead to big consequences. To avoid this, a soli internal data active defense strategies for Kaseya style ransomware attacks is required. This can done by monitoring the behavior of devices.
Behavioral analysis can use to identify anomalous behaviors that may indicate an attack. Although it can take a bit of investment to implement, it is important to detect attacks early.
For example, if an organization notices a change in device behavior or a spike in malware activity, it might be due to a malicious software update. It might be a good idea to engage forensic experts to determine the damage caused by the attack.
Exploitation as the initial access vector
Kaseya is a virtual system administrator (VSA) product that use to manage and operate customer infrastructure. It widely used by managed service providers in the US and the UK. Despite being a powerful tool, it is vulnerable to attack.
A recent ransomware attack against Kaseya was a prime example of exploits in action. The attackers used a zero day security flaw to bypass authentication and subsequently execute a malicious payload. The zero-day flaw discovered by the Dutch Institute for Vulnerability Disclosure.
The zero day exploit allows an attacker to run arbitrary commands on the targeted server, which can lead to code execution. While this is not the first ransomware attack to exploit a zero day, it is the first to exploit a zero day in the context of a supply chain attack.
Threat actors move faster than organizations can patch
With the rapid rise of ransomware attacks, organizations must take active defense strategies to prevent them. Specifically, they should implement good cyber hygiene, such as patching software, avoiding vulnerabilities, and updating systems.
In addition to updating their systems, organizations should review their business continuity plans and take other preventive security measures. For example, they should use Application Whitelisting Security, which prevents malicious code from running on their computers and keeps their systems on premise.
In the past year, cyber-threat actors have gotten smarter and faster. This often reflected in their exploitation of known vulnerabilities. For example, the REvil ransomware group exploited vulnerabilities in the Kaseya VSA software, bypassing authentication controls. Then, they uploaded a malicious payload to hundreds of companies and closed hundreds of schools.
In addition, Iranian state-backed threat actors have been exploiting Fortinet vulnerabilities since March 2021. They have also launched data exfiltration and extortion campaigns.
Thales ransomware group leaked 9.5 GB archive
A recent Kaseya style ransomware attack has impacted thousands of customers. It is one of the first attacks to exploit a zero-day vulnerability. The attackers used vulnerabilities in the VSA software to deliver their payload to clients. An active defense strategies for Kaseya style ransomware attacks is essential for all type of organizations.
The REvil gang is also known for its attacks on beauty salons, dentists, and childcare centers. It has been responsible for 300 ransomware campaigns per month.
In the first half of 2021, REvil has already exceeded the amount of money it made last year. During that period, the gang pushed out hundreds of ransomware campaigns to hundreds of targeted customers.
In addition to attacking businesses, REvil has also been known to target schools. As a result of the attacks, over 1,000 organizations had their servers encrypted. Some companies have paid the ransom, while others did not.